OAuth 2.0 Demystified: Four Authorization Grant Types
The OAuth 2.0 Authorization Framework specifies four grant types: authorization code, implicit, resource owner password, and client credentials. This post describes the four flows at a high level.
According to the OAuth 2.0 Authorization Framework (RFC 6749) an authorization grant represents the authorization, given by the resource owner, to a client to access protected resources on its behalf.
Continuing from the four roles blog post, the client is the mobile application wanting to retrieve the banking transactions on behalf of the user or, the resource owner.
The high-level authorization flow is shown in the diagram below:
OAuth 2.0 specifies four different grant types viz. authorization code, implicit, resource owner password credentials, and client credentials.
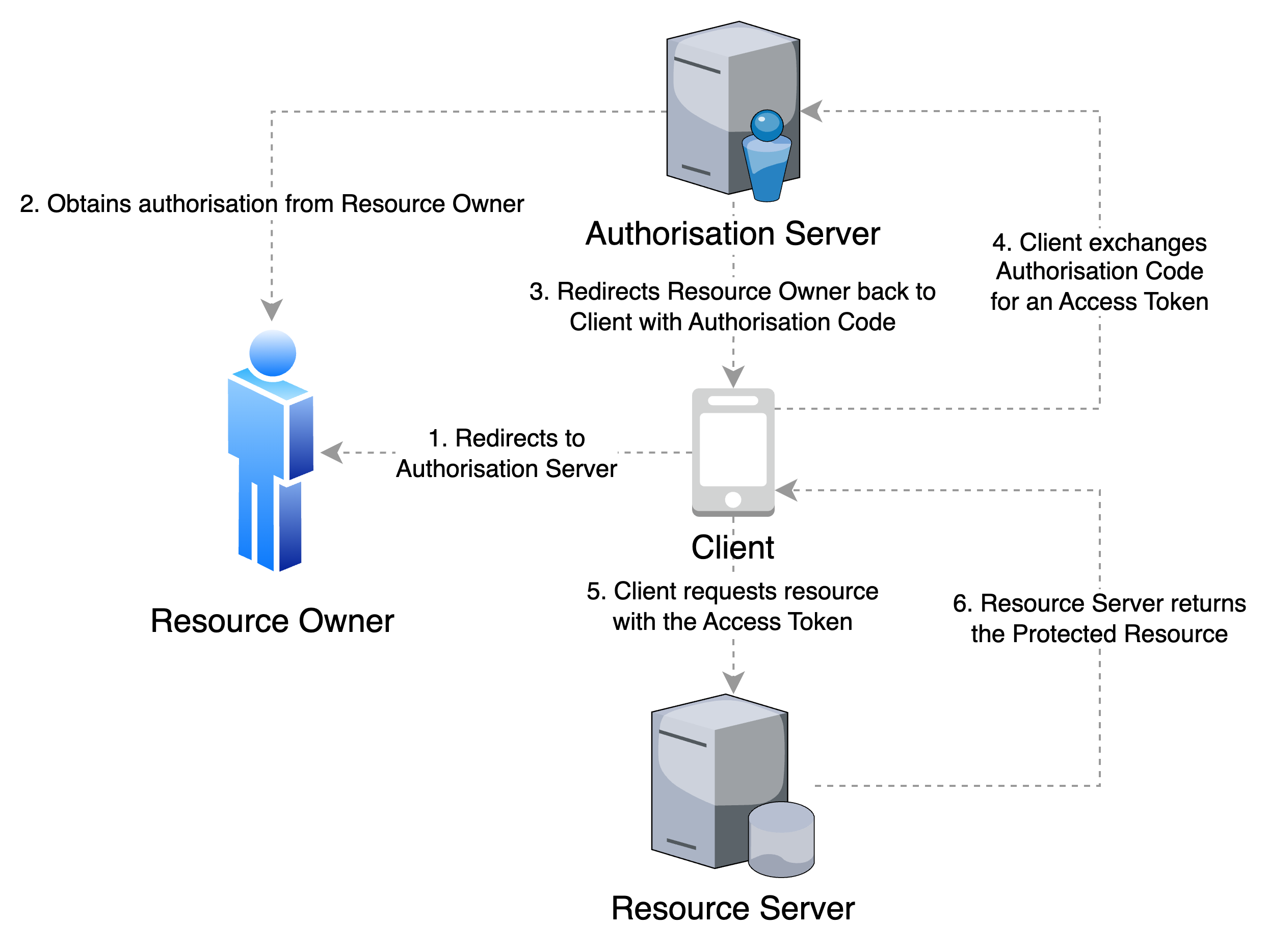
Authorization Code
In this flow, the Authorization Server issues an authorization code to the Client after obtaining authorization from the Resource Owner. The Authorization Code can then be exchanged for an Access Token, typically as a JSON Web Token (JWT).
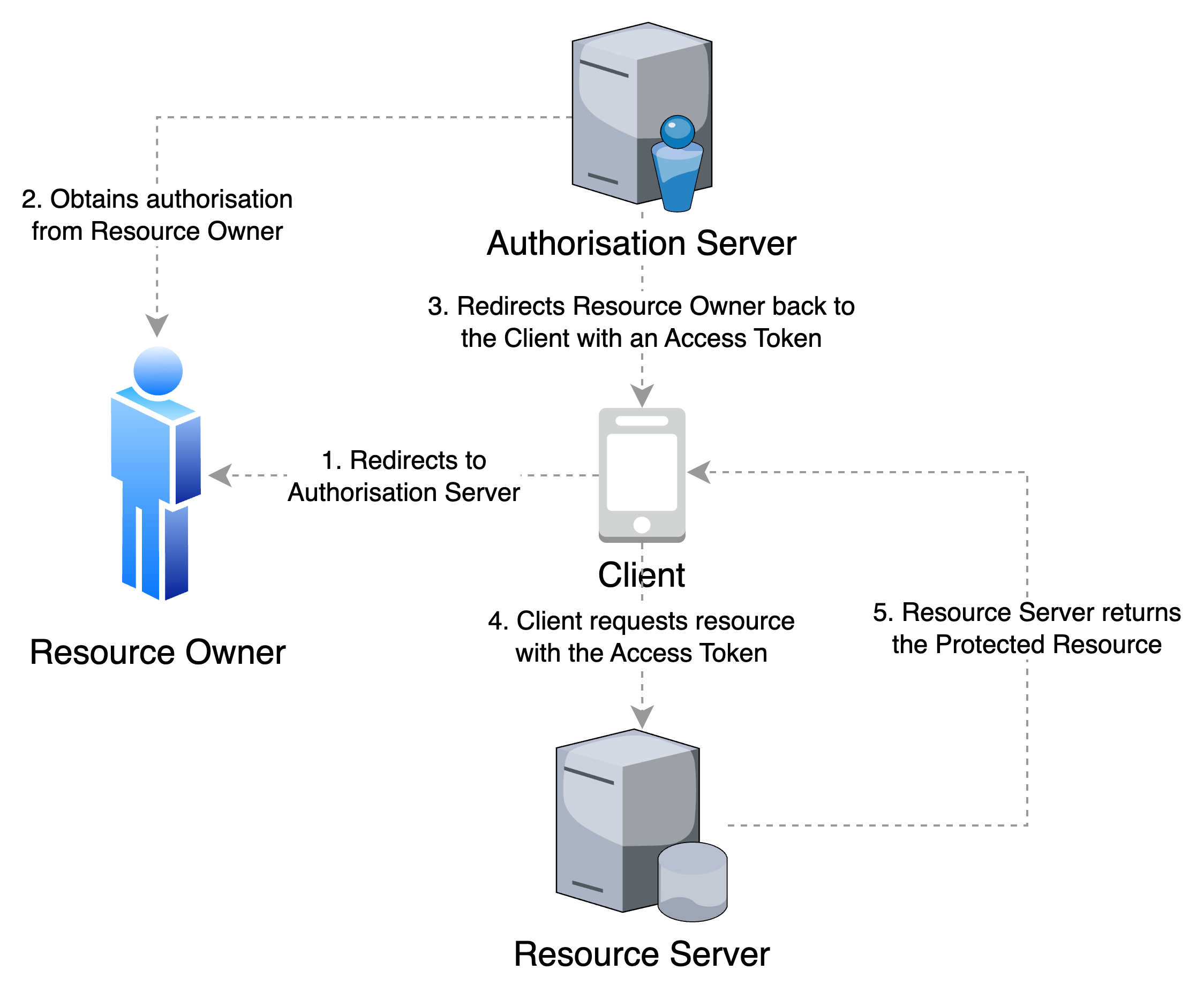
Implicit
In this flow, the Authorization Server issues an Access Token directly to the Client after successfully obtaining authorization from the Resource Owner. This grant type is "implicit" because no intermediate credentials are issued.
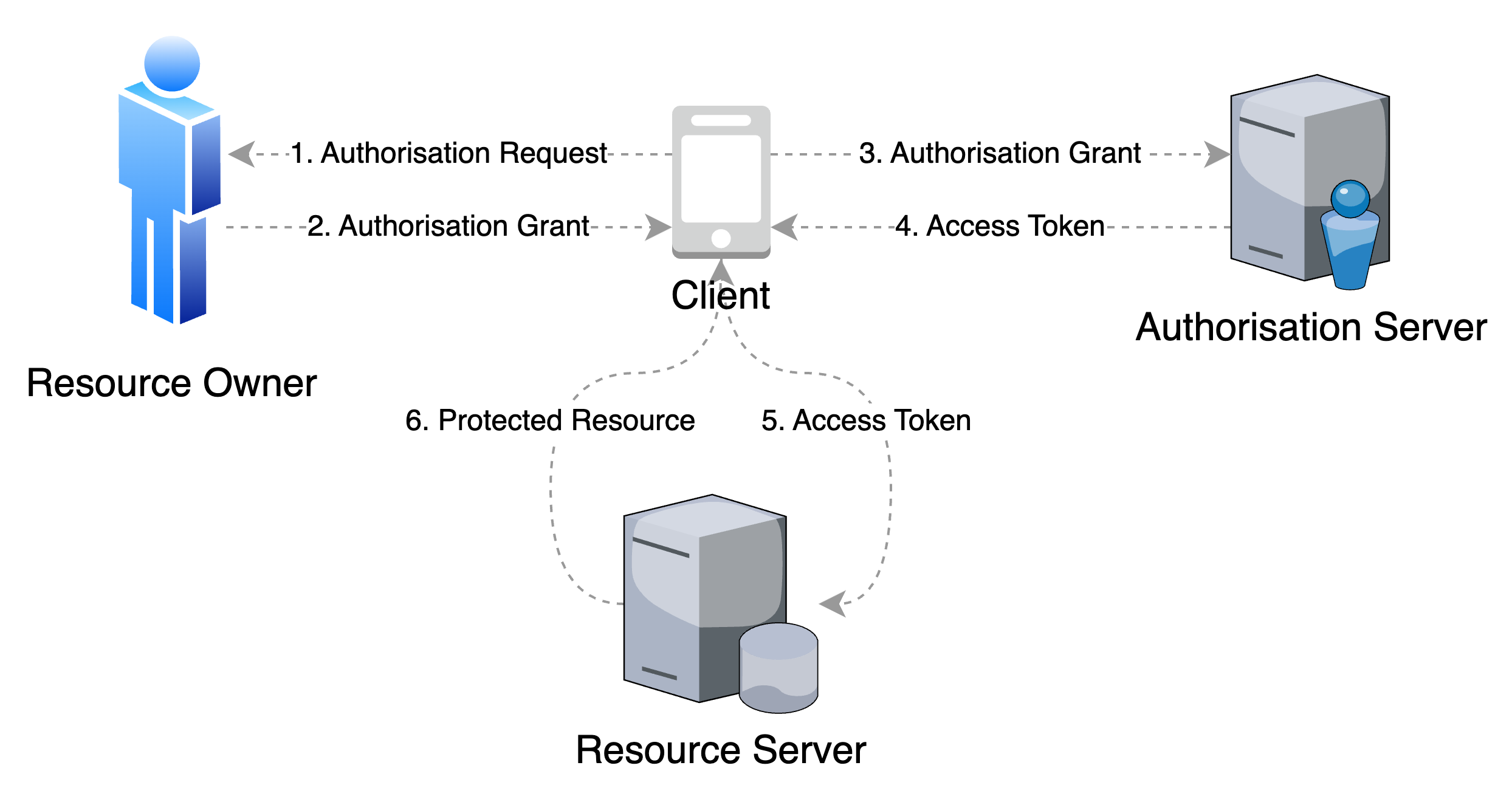
Resource Owner Password Credentials
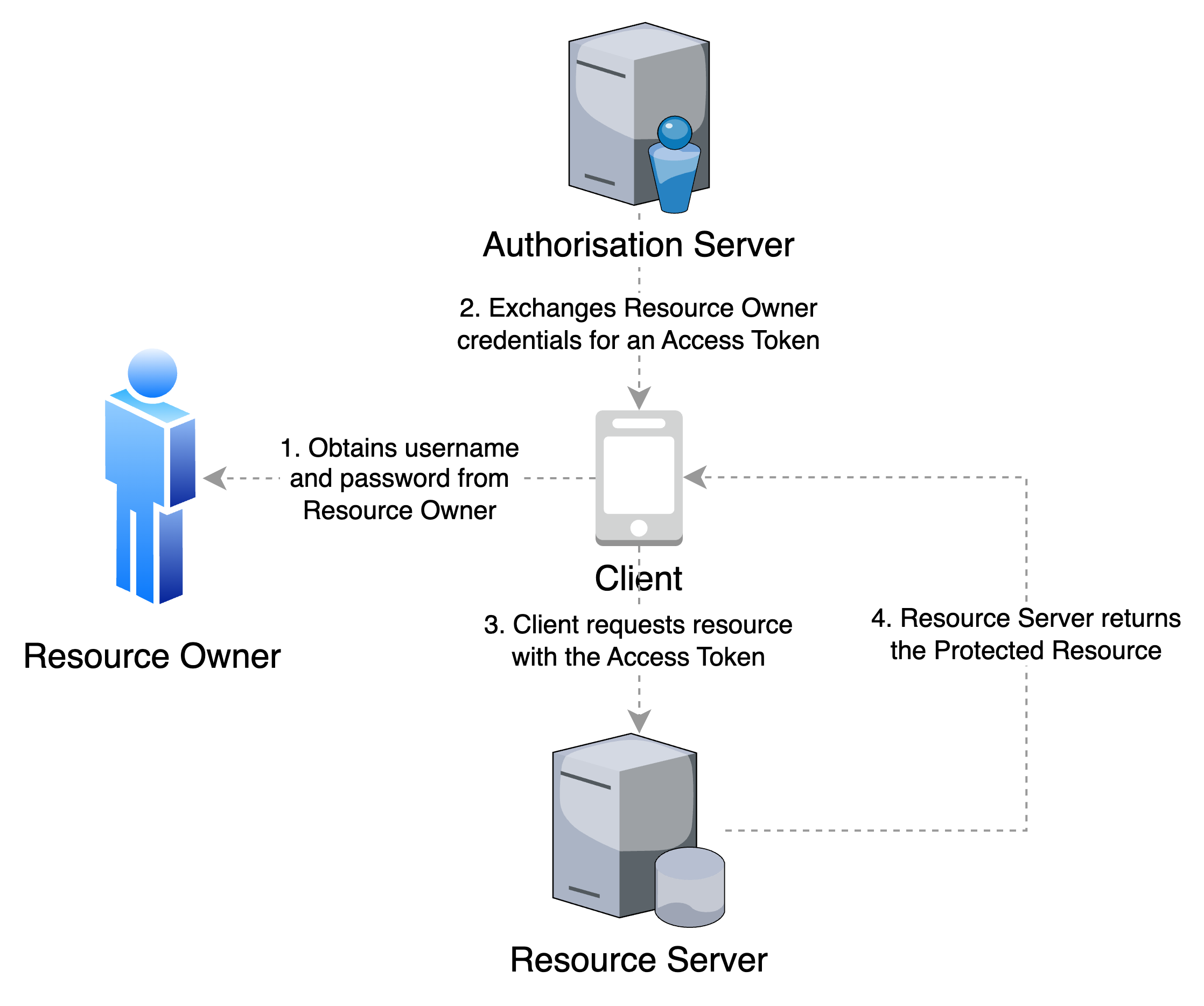
In this flow, a Resource Owner's password credentials are obtained by the Client and used as an authorization grant by the Authorisation Server to issue an Access Token to the Client.
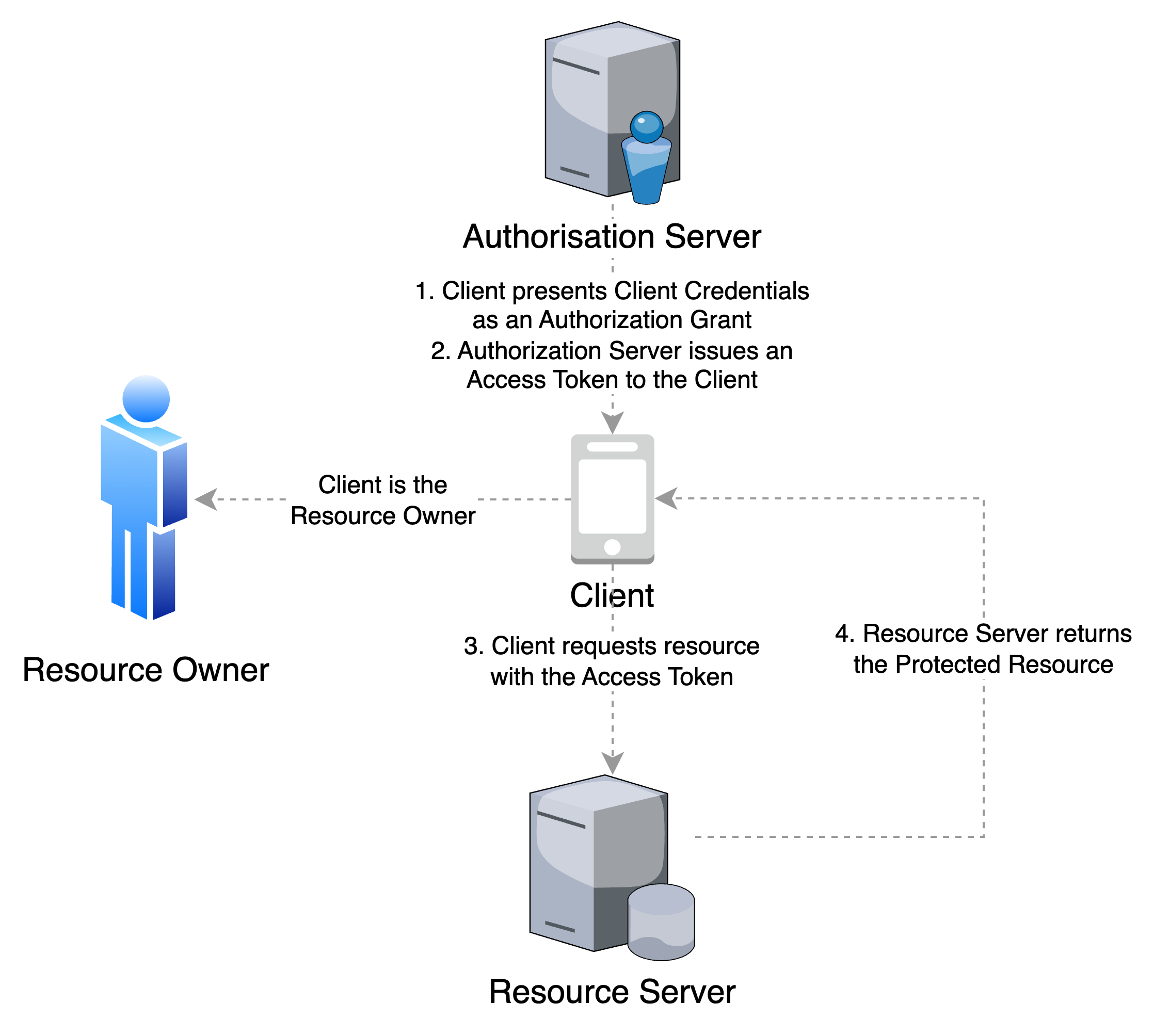
Client Credentials
In this flow, the Client is the Resource Owner and acts on its own behalf. The Client credentials are used as an authorization grant.